NCCS Cyber Security Solutions
At NCCS (National centre for cyber security), we specialize in developing cutting-edge cyber security solutions to help protect businesses and organizations of all sizes.
Our products range from advanced SIEM systems to network security solutions, all designed to keep your data and systems safe from cyber threats. Browse our selection to find the perfect fit for your organization.
We're developing cyber security products that combine innovation and
technique to cater all domains of the digital world
Our featured products are:

STIP (Security & Threat Intelligence Platform)
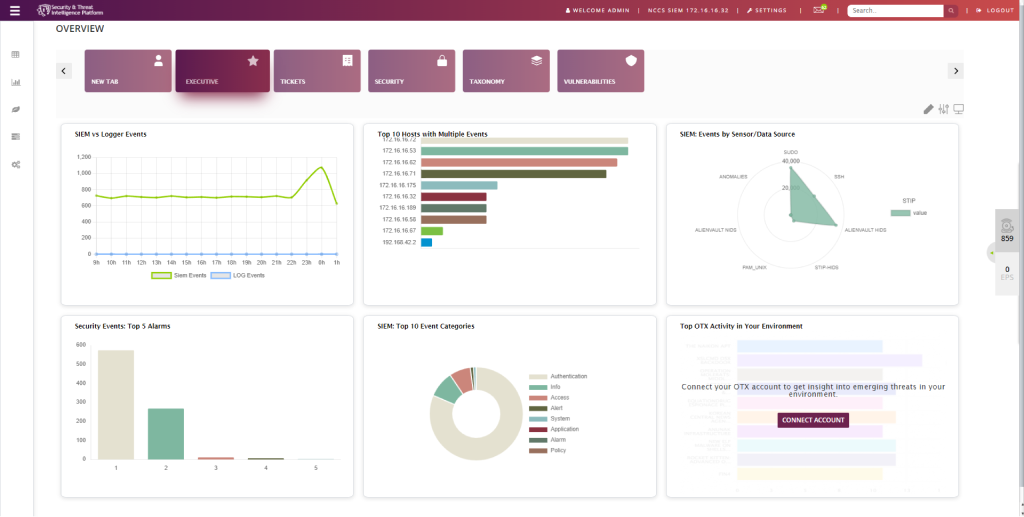
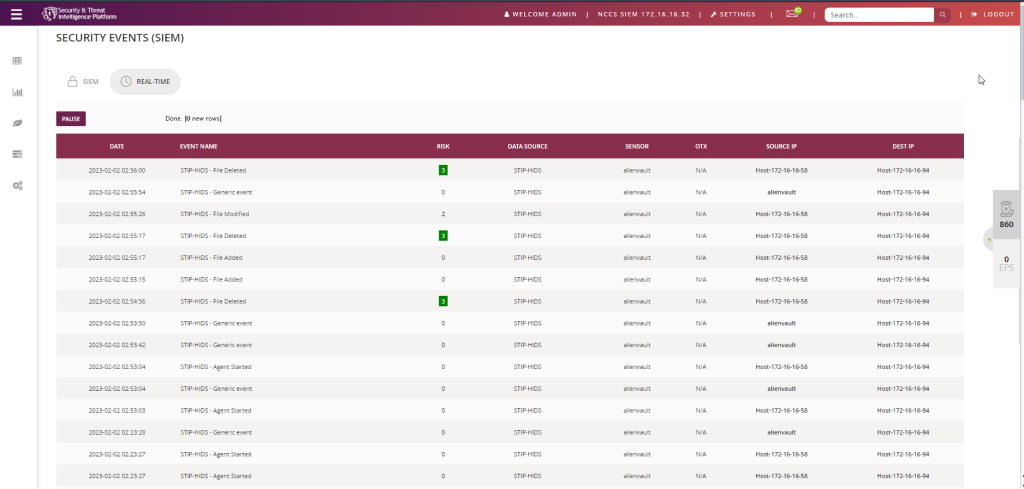
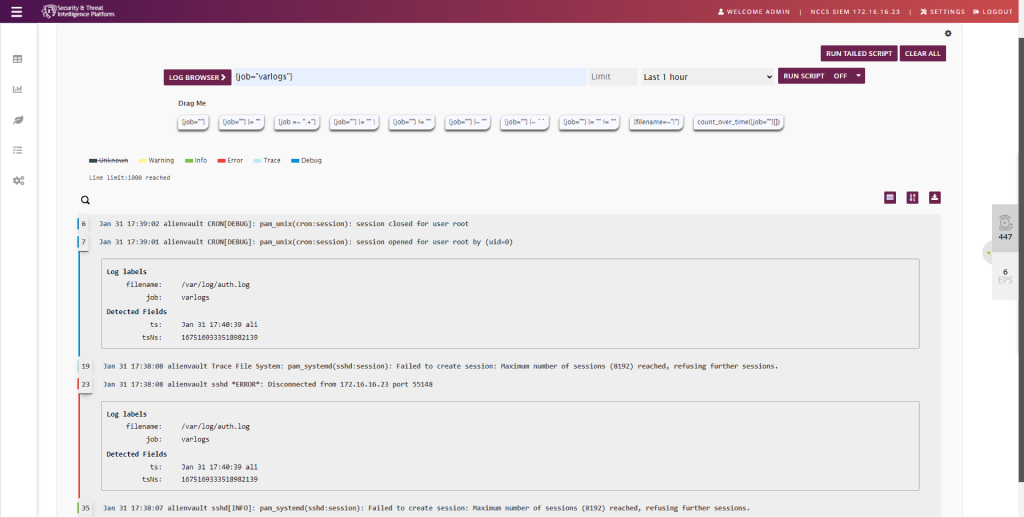
STIP is a security information and event management (SIEM) solution that allows users to monitor and analyze security-related data from various sources, such as network devices, servers, and applications. It can be used to detect and respond to security threats, as well as to perform compliance reporting and incident management. STIP includes features such as real-time event correlation, asset management, raw logging, plugin builder, file discovery and reporting.
STIP includes a SIEM system that can collect, correlate, and analyze log data from various sources to provide a comprehensive view of network security. It can be run on Linux and Windows operating systems.
Previews:
Noteworthy Features:
- Intrusion Detection and Prevention (IDP): STIP includes a built-in IDP system that can detect and prevent malicious network activity.
- Vulnerability scanning: STIP includes a vulnerability scanner that can identify vulnerabilities in your network and provide recommendations for remediation.
- Compliance reporting: STIP includes compliance reporting features that can help organizations meet regulatory requirements such as PCI-DSS.

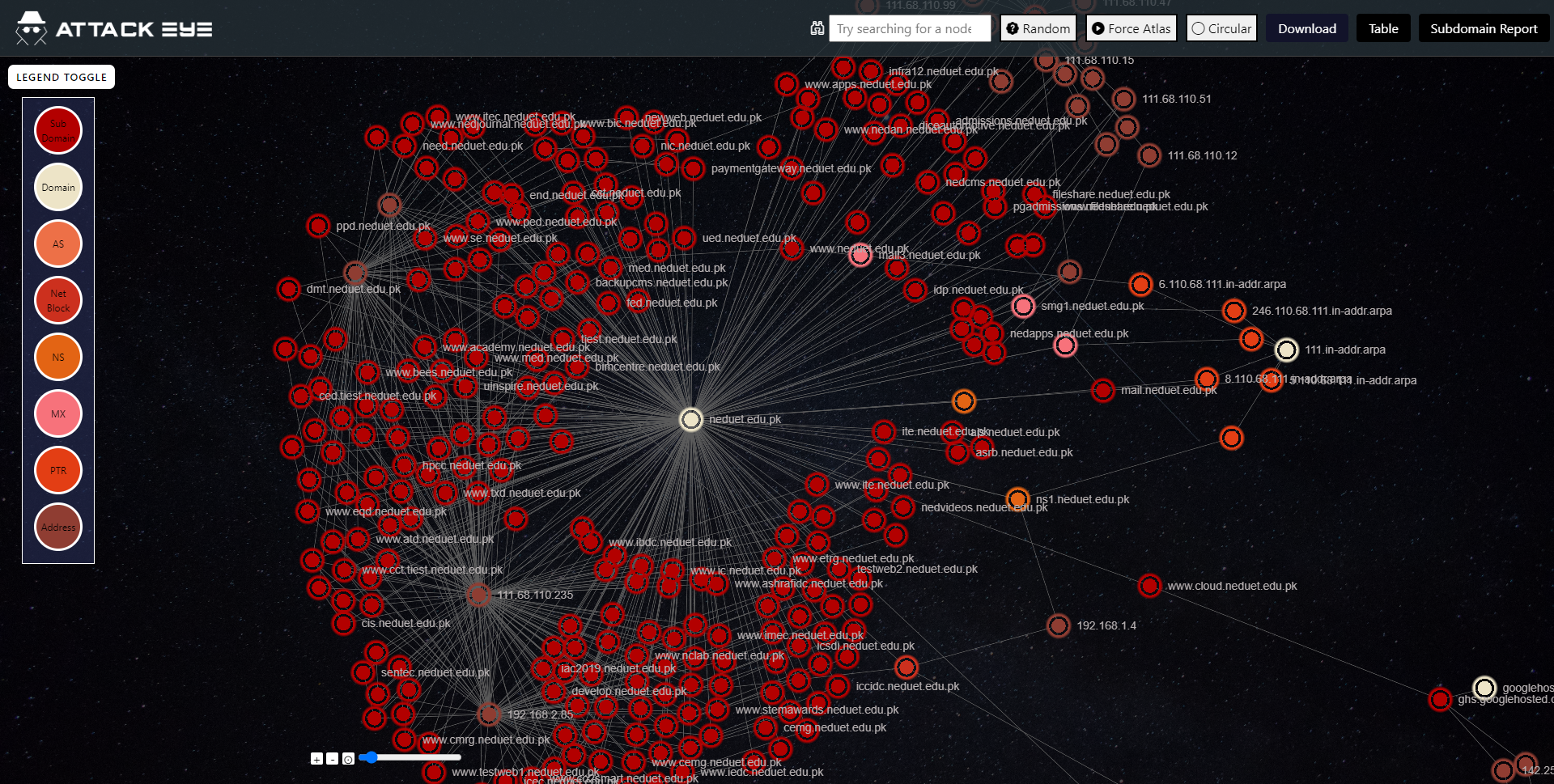
External Cyber Attack Surface Monitoring Solution
Attack eye is a powerful cyber security tool that analyzes domains and creates a map of interconnected nodes, including mail servers, cloud servers, and data servers. This map provides a comprehensive view of a domain's infrastructure, helping organizations identify potential vulnerabilities and protect themselves from cyber threats. With Attack eye, you can gain a deeper understanding of your domain's security posture and take proactive steps to secure your systems and data.
Previews:
Highlights:
- Subdomain enumeration, Port scanning, Domain reconnaissance, Vulnerability assessments and reporting using information from open source intelligence (OSINT) tools and other sources.
- Attack Eye presents the identified vulnerabilities and recommendations for mitigating them to users through a user interface element.
- The user interface element allows the application to present information to users in an easy-to-understand format.
Interested in integrating?
Send us a message and we will get back to you with a quote.
Send us a message